In my network configuration, some of my Docker containers, for example DNS, need to achieve high availability with Anycast. In my previous post , I created a Busybox container and run tail -f /dev/null , in order to let it persist infinitely, but without using any CPU cycles, to maintain a network namespace used by both the server application and BIRD. In short: I invented a Pod in Kubernetes on my own. I don't use K8S, since my nodes run individually rather than in a cluster, I don't need the cluster functionality of K8S at all. In addition, K8S is difficult to set up. But on another thought, a Busybox container seems like an overkill for this purpose, and I have to set the entrypoint manually. It would be great if I have a tiny Docker image that only sleeps indefinitely. Plan A:...
Static Build Tiny Docker Images
What's stored in Docker images can be seen as numerous tiny Linux systems. Most of them are based on Debian, Ubuntu, or Alpine, with extra software installed on top. Using a complete Linux distribution as the basis gives the benefit of having commonly used commands available, such as ls and cat . They are often used in the image-building process. In addition, they have comprehensive libraries of software packages, allowing users to create images that "just work" with apt-get . However, as soon as the image is built, these utilities become unnecessary burdens for disk space. In addition, a full Linux contains a service managing daemon, like SystemD or OpenRC, useless for Docker containers running only one program at a time. Although Docker images are "overlaid",...
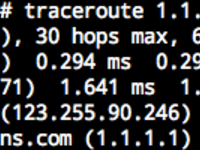
Writing Stories in Traceroute, Elegantly
Traceroute is one of the popular tools for network inspection. It shows the IP addresses of routers on the route from your computer to a destination server, similar to: Domains are shown on the last 2 hops, which is the IP's reverse DNS record. Reverse DNS records exist as PTR records in the format of 4.3.2.1.in-addr.arpa . For more information, you may refer to Setting IP Reverse Records in DN42 (Chinese Only) . Naturally, where there are characters, there will be stories shown in them. Two years ago, I set up a bunch of Docker containers, and modified and chained their routing tables, so they create the path needed for showing the essay . Using a lot of containers isn't elegant enough, and is a management burden, especially if the path is long....
Disabling TR069 on a Youhua PT926G Fiber Optic Modem
This post explains the procedure to disable TR069 on a Youhua PT926G fiber optic modem, to prevent China Telecom from pushing config/firmware updates, and void your change of switching to bridging mode or setting port-forward rules. In the WAN settings of the management portal of this modem, the TR069 connection can neither be modified nor removed. But with a simple patch on the management portal's code, you can break the limitation on the modem. First, you should follow my previous post: Hacking a Youhua PT926G Fiber Optic Modem , to obtain the Telnet Root password. Then Telnet in, run su , and type in the password to get to Root Shell. When you do that correctly, the command-line will prompt # . Then follow these steps: Type cp /home/httpd/web/net_eth_links.asp /var/ and hit Enter....
Planning Ahead: Using Post-Quantum Cryptography
On the modern Internet, most websites already support HTTPS. The SSL/TLS encryption protocol will encrypt users' requests and the website's responses so that malicious users along the way cannot steal or tamper with the information. One important component of SSL/TLS protocol is asymmetric cryptographic algorithms. For these algorithms, the key separates into a public key and a private key , with the public key being public and the private key protected carefully. Accessing an HTTPS website usually follows these procedures: The website sends its public key (as a certificate) to the browser. The browser will verify the public key in case that a man-in-the-middle modified the key in order to block or tap into the communication. The browser (or the operating system)...
Self-hosting a DNS Root Server
With the scale of conflict between China and the United States increasing, on some social media websites in China, some users started expressing concerns for the United States cutting China's access to DNS root servers or removing China's domains in the root servers in order to break China's Internet. By now, there is much analysis on the matter that states that this is unlikely to happen. Most of them focus on the following two points: DNS root servers use Anycast to broadcast their IPs, and there are root servers present in China that won't be affected by the network cut; For the United States, shutting down root servers cause more trouble than benefit, both economically and politically. Yet today, I'm going to present another point:...
Hacking a Youhua PT926G Fiber Optic Modem
This post explains the procedure to obtain such privileges from a Youhua PT926G fiber optic modem, without disassembling the device or using serial port converters. Super Admin users on Web UI (telecomadmin) Telnet's root user access FTP access FYI I obtained the device from China Telecom, Guangdong Shenzhen. Log on as Super Admin If you directly access the modem's IP ( http://192.168.1,1 ), you will see such a login page to the modem: Here you can log in with account name useradmin and the password labeled on the back of the modem, but there's not much you can do once logged in. The only useful thing seems to be Wi-Fi setting. But a Nmap scan reveals much more: $ nmap -v 192.168.1....
An Elegant "Scripture of Safety" Generator
This post is about a meme in China that may require some cultural background to understand. Since the content is related to the specific language used, there are minor differences between the Chinese and English versions. What's "Scripture of Safety"? The Scripture of Safety (平安经) is a book written by He Dian, the (now former) official of Jilin Public Security Department, China. The content in the book is simply a repetition of the phrase "Wish XXX safe" (XXX 平安), yet the book is sold at a high price. The public speculates that publishing and purchase of the book serves as a mean of bribe. The content of The Scripture of Safety is formatted as: (from Wikipedia (Chinese) ) 「眼平安,耳平安,鼻平安」 "Wish eyes safe, ears safe,...

Intel and NVIDIA GPU Passthrough on a Optimus MUXless Laptop
Changelog 2022-07-21: Add starting GVT-g on startup. Thanks to comment from Owsmyf (on Chinese version of this post). 2022-01-22: Revisions on NVIDIA driver updates and comments. I successfully passed through an Optimus MUXed GPU on my new laptop. Abstract (Spoiler Alert!) I successfully passed through Intel's GVT-g virtual GPU, as well as the dedicated NVIDIA GPU itself, into a virtual machine on Lenovo R720 gaming laptop. However, due to the limitation of the architecture itself, this GPU passthrough scheme is severely limited. For example, the dGPU is unusable in many games, and the performance is still relatively worse despite the complicated setup it needs. Therefore, you may attempt the passthrough purely for the fun of tinkering,...
Graduation Design - Sensor Network Development Log
Welcome to my third development log. In the two previous logs, I discussed the pitfalls I met in the RoboMaster competition and FPGA course final project . This time I will be talking about my graduate design project, an air quality sensor network built by a 3-person group. The whole project is structured as follow: Obtain data from installed sensor modules and upload them to InfluxDB running on a server Sensors we used: MiCS6814, measures NO2, CO, and NH3 Analog output BME680, measures temperature, humidity, atmospheric pressure, and TVOC I2C interface PMS5003, measures particle matters UART serial output Extra modules: ATGM336H, global positioning module with GPS+BeiDou support UART serial output ESP8266, a widely used Wi-Fi module UART serial output MH-CD42,...