Preface Almost four and a half years ago, I migrated the blog's site system from Typecho to Hexo (Chinese only link) . Hexo is a static site generator that by itself doesn't connect to databases like MySQL and PostgreSQL and dynamically generate pages. Instead, it generated all HTML pages in one go based on the given Markdown files. Compared to dynamic solutions like WordPress and Typecho, pre-generating static pages eliminates the need of dynamic language support on the web server (like PHP), and has lower performance requirements on the server. Hexo itself, however, is not a new solution. It's first version was released back in July 2013 . By then, single page application frameworks, leaded by React, were just released (React: May 2013)....
How to Kill the DN42 Network (Updated 2023-05-12)
DN42, aka Decentralized Network 42, is a large, decentralized VPN-based network. You can read more about DN42 in this post: DN42 Experimental Network: Intro and Registration DN42 is an experimental network , where everyone helps everyone. Nobody is going to blame you if you screwed up. You may seek help at DN42's IRC channel , mailing list or the unofficial Telegram group . Since DN42 is a network for experimentation, a lot of relatively inexperienced users also participate in it. Therefore, occasionally an inexperienced user may misconfigure his/her system and impact the whole DN42 network or even shut it down. As a more experienced user,...
Low-cost GeoDNS with NS1 and UptimeRobot/Freshping
Some parts of the content come from https://hostedtalk.net/t/connecting-uptime-robot-with-ns1-dns-api/3883 。 Goal I have quite a few VPSes around the world, but my website had been served by a single VPS in Los Angeles for a long time. Because I purchase VPSes from small providers for their specific routing configuration or low price, the network of this VPS can be unstable from time to time. Although it's rare, I had to manually point the DNS to another VPS in case of an outage and switch back after it's back up. Therefore, I want to serve my website with all my VPSes, and automatically reroute traffic to other VPSes if one VPS is down. Synchronizing website data is of no difficulty since I use Hexo, a static site generator....

NixOS Series 2: Basic Config, Nix Flake & Batch Deploy
List of NixOS Series Posts: NixOS Series 1: Why I fell in love NixOS Series 2: Basic Config, Nix Flake & Batch Deploy Recommended: NixOS & Nix Flakes - A Guide for Beginners by Ryan Yin NixOS Series 3: Software Packaging 101 NixOS Series 4: "Stateless" Operating System NixOS Series 5: Creating Disk Image for Low RAM VPS This is the second post in my NixOS series and mainly focuses on: Basic format of NixOS config files and how to edit them Flake functionality of Nix package manager Deploy-RS deployment tool This post assumes that you've installed NixOS with NixOS's official installation manual . Changelog 2023-05-10: Add a recommended post: NixOS & Nix Flakes - A Guide for Beginners by Ryan Yin. 2021-12-18: NixOS 21....

NixOS Series 1: Why I fell in love
List of NixOS Series Posts: NixOS Series 1: Why I fell in love NixOS Series 2: Basic Config, Nix Flake & Batch Deploy Recommended: NixOS & Nix Flakes - A Guide for Beginners by Ryan Yin NixOS Series 3: Software Packaging 101 NixOS Series 4: "Stateless" Operating System NixOS Series 5: Creating Disk Image for Low RAM VPS Right now, I'm gradually migrating my servers from Devuan Linux to NixOS . NixOS is a Linux distribution centered on a set of Nix configuration files located in /etc/nixos , which is used to install and configure the whole operating system. Because this configuration set defines ALL config files and packages on the system, as long as you use the same config files, you will absolutely get the same operating system every time you reinstall....
Replace Jenkins with Drone CI
Jenkins is a free and open-source CI/CD software widely used in all kinds of scenarios. The main advantage of Jenkins is its grand collection of plugins capable of all sorts of jobs, including deploying with SCP or Ansible , analyzing code with Cppcheck , and notifying job status with Telegram or DingTalk . Previously I also used Jenkins for automation of numerous jobs, like rebuilding my Docker images , deploying the blog you're visiting right now, and even auto sign-in to Genshin Impact . But Jenkins is a CI with a long history, and its predecessor Hudson was released back in 2005. Therefore, Jenkins executes commands directly when it comes to running jobs instead of using modern approaches such as containers....
Lookup Any Public WHOIS with this nginx-based Server
After I set up a DN42 WHOIS server with Nginx , I configured my DN42 Looking Glass to use this service. As my Looking Glass is capable of running as a Telegram bot, fellow group members are looking up WHOIS information of IPs and domains with it. But soon we noticed a problem. A significant part of members have applied for ASNs and IP ranges on the public Internet after they're familiar enough with DN42, and they're peering at Internet Exchange Points. Therefore, they often need to lookup some public Internet IPs, ASNs, and domains, yet none of the Telegram bots in our group can do so. It would be quite helpful for us if there exists a WHOIS server that proxies lookups to relevant registries. Proxying is exactly what Nginx is good at. With some modifications to Nginx,...
DN42 Experimental Network: Intro and Registration (Updated 2022-12)
DN42, aka Decentralized Network 42, is a large, decentralized VPN-based network. But unlike other traditional VPNs, DN42 itself doesn't provide any VPN exits, which means it doesn't allow you to bypass Internet censorships or unlock streaming services. On the contrary, the goal of DN42 is to simulate another Internet. It uses much of the technology running on modern Internet backbones (BGP, recursive DNS, etc), and is a great replica of a real network environment. In short, DN42 is: NOT suitable for users only seeking privacy protection or bypassing censorship NOT suitable for users consuming large amounts of bandwidth/data, such as for unlocking streaming services IS suitable for users learning about networking, practicing configuration of servers and routers,...
Setting up DN42 WHOIS Server with Nginx
In my previous post, " Setting up Gopher Site with Nginx ", I mentioned that the Gopher service is a byproduct of my original plan: modifying Nginx into a WHOIS server for DN42. This post will explore into details of that process. The WHOIS Protocol First, we can find a WHOIS server to observe its response. Choose the WHOIS server for .pub domain as an example, and run telnet whois.nic.pub 43 : # Type following line and hit enter lantian.pub # WHOIS server responded with: Domain Name: lantian.pub Registry Domain ID: c69e5ccf9d834900be26f88fddc5c9e4-DONUTS Registrar WHOIS Server: whois.dnspod.cn Registrar URL: https://www.dnspod.cn Updated Date: 2021-01-07T14:09:11Z Creation Date: 2016-10-23T08:36:41Z Registry Expiry Date: 2029-10-23T08:36:41Z Registrar: DNSPod, Inc....
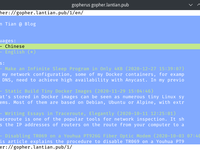
Setting up Gopher Site with Nginx
Changelog 2021-03-24: Improve post-processing, add scripts for parsing links and images. 2021-03-21: Initial version. What's Gopher Gopher is a protocol born in the early ages of the Internet. It was invented at the University of Minnesota in 1991, with a purpose similar to HTTP today. The protocol itself is extremely simple: Client connects to TCP port 70 of the server, and send one line of URL ending with CRLF, e.g. some_dir/hello.txt Server sends data of the requested file and closes the connection. And we're done. The server could be returning a text file, a picture, a binary file, or a Gopher list file called Gophermap with special formatting. Each line of the file is composed of the following fields: A character representing the type of this line, may it be text ( i ),...