Foreword SideStore is a commonly used iOS app sideloading tool that allows you to install third-party apps bypassing the App Store. It works by using your Apple ID to obtain a free Apple developer certificate, which is then used to sign the app you want to install, allowing it to run normally on your iOS device. However, to maintain control over the iOS ecosystem, Apple prevents third-party app stores from using developer certificates to bypass restrictions on a large scale, setting a 7-day expiration period for developer certificates. Users need to regularly obtain new developer certificates and re-sign their apps to continue using the third-party apps they have installed. Traditional sideloading tools, such as AltStore,...

Nix Logarithmic Math Library from Ground Zero
List of Nix Math Library from Ground Zero series posts: Nix Trigonometric Math Library from Ground Zero Nix Logarithmic Math Library from Ground Zero (current post) (Cover image from: Wikipedia - Logarithm ) Origin Due to a somewhat absurd reason (calculating the physical distance between VPS to estimate network latency), I implemented a somewhat absurd trigonometric function library using Nix . After I published the trigonometric function library on GitHub , I found that someone actually used it! It seems my needs weren't too absurd after all. In the repository's Issues, a user suggested that I add some exponential/logarithmic function support to this math library , such as exp , ln , pow , and log . Since implementing these basic functions from scratch is also quite interesting,...
Legal LTE Network at Home for $100
This post is automatically translated from the Chinese version with LLM. The translation content has been edited and verified by the author. Yes, you read that right. Without the need for Faraday cages or signal-blocking measures, you can build a legal LTE network at home (in the US) for around $100, capable of transmitting continuously 24/7. Regarding "legal": I am not a lawyer or a wireless expert. Based on my research into the relevant policies and regulations, my entire setup should be legal. However, I take no responsibility if you encounter any legal issues after following the instructions in this post. CBRS Band: Unlicensed LTE/5G Band in the US The challenge in building your own LTE network lies not in the technology but in legally acquiring radio spectrum resources....
Building Custom Android Kernel with Nix
Preface The mobile phone I'm using today is Motorola Edge+ 2023, an Android phone. To better customize my phone's functionalities, I unlocked its bootloader, and obtained root privileges, in order to install LSPosed and various LSPosed based plugins. The root mechanism I'm using is KernelSU , which works by modifying the Linux kernel to grant and only grant root permissions to certain apps. Although KernelSU provides official GKI kernel images that work on most phones, I also flashed LineageOS onto my phone, which is not compatible with GKI images. Therefore, I have to compile my own kernel. Since modifying the kernel's binary image is difficult, we usually obtain the kernel source code under the GPLv2 license from the phone manufacturer, modify it according to KernelSU's official guide ,...
Migrating My Blog to Astro.js
Preface Almost four and a half years ago, I migrated the blog's site system from Typecho to Hexo (Chinese only link) . Hexo is a static site generator that by itself doesn't connect to databases like MySQL and PostgreSQL and dynamically generate pages. Instead, it generated all HTML pages in one go based on the given Markdown files. Compared to dynamic solutions like WordPress and Typecho, pre-generating static pages eliminates the need of dynamic language support on the web server (like PHP), and has lower performance requirements on the server. Hexo itself, however, is not a new solution. It's first version was released back in July 2013 . By then, single page application frameworks, leaded by React, were just released (React: May 2013)....

NixOS Series 5: Creating Disk Image for Low RAM VPS
List of NixOS series posts: NixOS Series 1: Why I fell in love NixOS Series 2: Basic Config, Nix Flake & Batch Deploy NixOS Series 3: Software Packaging 101 NixOS Series 4: "Stateless" Operating System NixOS Series 5: Creating Disk Image for Low RAM VPS (current post) Black friday has passed. Some readers, I believe, have perchased some VPSes or cloud servers on sale, and want to install NixOS on them. However, since NixOS is nowhere as famous as popular Linux distros, such as CentOS, Debian and Ubuntu, almost no VPS provider will offer a disk image preinstalled with NixOS. This lefts the user one of the following options to perform the installation manually: Mounting NixOS's installer ISO, and then partition and install manually....
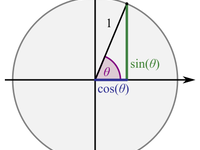
Nix Trigonometric Math Library from Ground Zero
List of Nix Math Library from Ground Zero series posts: Nix Trigonometric Math Library from Ground Zero (current post) Nix Logarithmic Math Library from Ground Zero (Cover image from: Wikipedia - Trigonometry ) Why I wanted to calculate the network latency between all my VPS nodes, and add the latency into the configuration file of Bird BGP daemon, so the network packets are forwarded through the lowest latency route. However, I have 17 nodes as of today, and I didn't want to manually run a ping command between each pair. So I came up with a solution: I can mark the latitudes and longitudes of the physical locations of my nodes, calculate the physical distance, and divide that by half the light speed to get the approximate latencies. I randomly sampled a few node pairs,...

Preventing Pipewire from being SIGKILLed
Problem I frequently encounter the situation that the Pipewire audio server is suddenly stopped: The problem usually appears when I connect/disconnect my laptop from the power adapter. My computer usually lags for a short time while switching between performance profiles. systemctl --user status pipewire.service only shows that the Pipewire process was terminated by a SIGKILL signal, without any other useful log information. Neither coredumpctl nor dmesg shows the existence of a core dump event. Cause The Pipewire process runs with realtime priority, with which its scheduling needs are satisfied first, so it can process audio data in time to prevent stuttering. To increase its process priority,...
How to Kill the DN42 Network (Updated 2023-05-12)
DN42, aka Decentralized Network 42, is a large, decentralized VPN-based network. You can read more about DN42 in this post: DN42 Experimental Network: Intro and Registration DN42 is an experimental network , where everyone helps everyone. Nobody is going to blame you if you screwed up. You may seek help at DN42's IRC channel , mailing list or the unofficial Telegram group . Since DN42 is a network for experimentation, a lot of relatively inexperienced users also participate in it. Therefore, occasionally an inexperienced user may misconfigure his/her system and impact the whole DN42 network or even shut it down. As a more experienced user,...
NVIDIA GPU Passthrough on an Optimus MUXed Laptop (Updated 2023-05)
A year ago, to simultaneously browse webpages and write codes on my Arch Linux installation and use Windows to run tasks infeasible on Linux (such as gaming), I tried GPU passthrough on my Lenovo R720 gaming laptop . But since that laptop has an Optimus MUXless architecture (as mentioned in that post), its dedicated GPU doesn't have output ports, and the integrated GPU is in charge of all the displays. Therefore, severe limitations exist for that setup, and I eventually gave up on it. But now, I've purchased a new laptop. The HDMI output port on this laptop is directly connected to its NVIDIA dedicated graphics card, or in other words, it has an Optimus MUXed architecture. Since there is a way to make the virtual machine aware of a "monitor on the dedicated GPU",...